Detect, Respond and Recover
Pegasus’ mission as an Intelligent Security Service Provider (iSSP) is to offer our customers complete solutions associated with the best and most specialized professionals, processes and technologies.
Our solution is based on 3 pillars:
X-VRM
Vulnerability and Threat Management

Vulnerability Scanning
Benchmarking & Third Party Risks
Penetration Testing
Red Team
Threat Hunting Management
X-THREATS
Threat Intelligence

Data Protection Risk
Threat Intelligence Feeds
Custom Intelligence Projects
X-SECURE
Detection & Response

Asset Protection
Detection and Response Management
Incident Response & Digital Forensics
Managed Security
Now that the boundaries of information and data within companies have disappeared due to digital transformation, it is essential to adapt to a new approach to security.
Pegasus Security, as a security service provider, has a holistic view: we must help our customers maximize the protection of their business against cybersecurity threats and minimize the risk according to their needs and capabilities.
Pegasus Security manages all security elements that are used to limit or prevent threats and attacks from succeeding.
It is important to cover the different possible attack vectors and ensure that all basic protection mechanisms are in place, helping to minimize the risk associated especially with the most vulnerable, such as employees, email or mobile terminals.
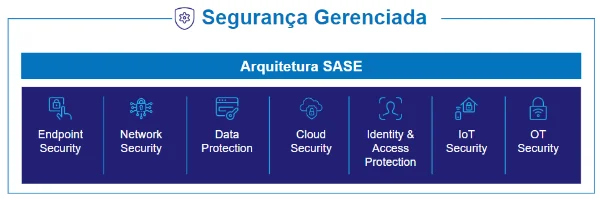
Device Security
The device is the primary gateway used by attackers to compromise an organization.
Traditional security solutions protect the network (firewalls, IDS, DLP, etc.), but do not protect against risks arising from the new digital ecosystem, such as: employees working outside the corporate network, obfuscated traffic or Shadow IT / IoT.
As traditional signature-based antivirus is insufficient for today’s attacks, we need new strategies to effectively fight sophisticated attacks that employ advanced malware, exploits, or APTs.
Network Security
The concept of network security no longer works alone due to the drastic challenges of digital transformation: Pegasus Security is the perfect partner to offer a single network and security solution to its customers.
- User mobility
- Migration to the Cloud
- The evolution of threats
- SD-WAN Adoption
At Pegasus Security,
we understand these issues and have adapted our solutions to this complex landscape of diffuse edge ecosystems.
Secure access to and use of corporate application services.

Secure Internet browsing services
Secure access to and use of corporate application services.
Data Protection
Information is one of the most valuable assets of any company and represents a challenge when it must be protected:
- Where is it?
- Who accesses what?
- Is it sent?
- To whom?
What to protect…
User? Device?
Managed Security Services:
- SOCs with professionals specialized in the main technologies
- With Major Incident Response (CSIRT) capabilities
- Specialized Analysts
Security controls:
- Security tools
- Cutting-edge technology agreements and knowledge
Professional services:
- Auditing and Consulting
- Training
- Integration
Cloud Security
Public Cloud is an enabler for Digital Transformation, but its adoption brings different challenges for the business, of which Security is one of the most important.
As in public cloud environments, the responsibility for security is shared between the cloud provider and the customer, companies need a reliable partner like Pegasus Security in this complex journey.
A capabilities-based proposition for the entire cloud journey
- CWPP | Cloud Workload Protection Platform
- CSPM | Cloud Security Posture Management
- CASB | Cloud Access Service Broker
Identity and Access Protection
Identity and access protection is a cross-cutting need in the cybersecurity chain.
It is not only about who has access or not, but also how and when that access is granted.
Identification and authorized access must be granted based on an updated and ongoing risk assessment allocated to this access, password/certification lifecycle, digital signatures… which is sometimes overwhelming for organizations.
Our specialized consulting team
along with our portfolio of solutions support companies in building and implementing a customized Strategic Identity Plan.
Analysis and Design
Implementation
Monitoring
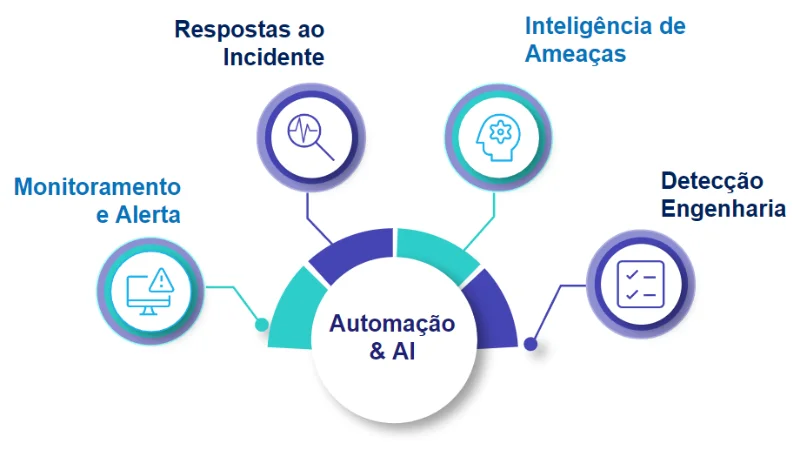
Enhanced Detection and Response Capability
Changing traditional security:
- Focus on behavior and post-breach via AI/ML
- EPP Extension 🡪 EDR and attack surface
- IDPS/FW extension 🡪 NTA/NDR capability
New “frontiers” to protect:
- Cloud Workload Protection, CASB, CSPM
- IoT / ICS Networks. Mobility. SD-Wan
- Digital risk protection (brand, reputation)
Extended Mission:
- Facilitate breach investigation, remote containment, and forensics
- Analytics layer with telemetry to enable AI detection & Hunting
Integrate parts and expand capabilities
X-Secure: Managed Detection and Response
Benefit from 24/7 continuous threat monitoring, breach investigation, and rapid remote response

Outsource 24/7 threat monitoring,
and breach detection and investigation efforts to our expert teams

Enhanced detection with X-Secure, including endpoint protection, deployed and maintained by our team

Our experts provide practical guidance on incident eradication and recovery, as well as rapid breach containment actions.
Our Differentiators
BEST ENDPOINT PROTECTION TECHNOLOGY
Extend your security investment with an advanced EPP solution, including EDR and attack surface capabilities, resulting from our premium agreements with best-in-class vendors
24×7 CENTER OF EXCELLENCE
The service is delivered by our 24/7 Global Centers of Excellence, leveraging global threat visibility and standardized automation of response, supported by our local capability
ADVANCED DETECTION AND CTI CAPABILITY
Our MDR platform extends the EPP protection layer through advanced detection analytics, orchestration capabilities, and the application of our proprietary intelligence
X-Secure: Managed Detection and Response
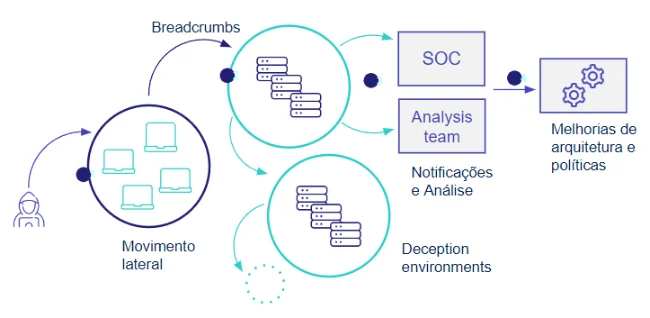
Leverage synthetic environments that attract and misdirect attackers while gaining intelligence
- Distract the adversary from the Client’s real assets and consume their resources for data.
- Identify vulnerable assets and shield infrastructure from targeted attacks.
- Discover internal or external threats
- Deploy security resources and budgets more efficiently
Our Differentiators
LEVERAGING COUNTERINTELLIGENCE TECHNOLOGY
We provide the technology to design and implement deception systems
CUSTOMIZABLE DECOY ENVIRONMENTS
Our deception services provide a wide range of deception environments capable of replicating different internal and external public-facing and DMZ networks.
CTI COLLECTION AND THIRD PARTY INTEGRATION
Counterintelligence technology leverages mapping with the ATT&CK framework and enables the consumption and recovery of attacker techniques/patterns to enable hunting efforts. Additionally, alerts can be easily exported to your SIEM
X-Secure: DFIR
Expand your CSIRT capability with 24/7 assistance in breaches and complex crises
- Ack Inquiry Assign Incid. Handler
- Evidence Collection 1st Contains
- Analysis & Initial Report
- Commitment Assessment Remediation Guidance
- Lessons learned and hardening
24/7 availability and support from our experts in malware remediation, digital forensics, threat intelligence, and crisis management
Dedicated incident handler, onsite/remote, coordinated response
Comprehensive guidance on remediation, lessons learned and legal support
Our Differentiators
LOCAL RESPONSE CAPACITY
Local presence for on-site crisis coordination and evidence management, supported by our global rapid analysis capability
END-TO-END INCIDENT ASSISTANCE
Support your team throughout the life of the incident, including full guidance on implementing remediation actions, system recovery, backup and protection
THREAT INTELLIGENCE
FORENSICS & ANALYSIS TOOLING
To support threat contextualization and CoAs for threat eradication, including our forensic tools for rapid deployment, evidence collection, and full IoC scanning
X-SECURE
- Managed Detection and Response (MDR)
- Actions for remediation and impact containment
- Digital Forensics

