X-VRM: Vulnerability Management
TestX-VRM: Application Security Testing
and automated testing to identify IT assets and applications and assess their vulnerabilities. Our Portal will help you prioritize your remediation
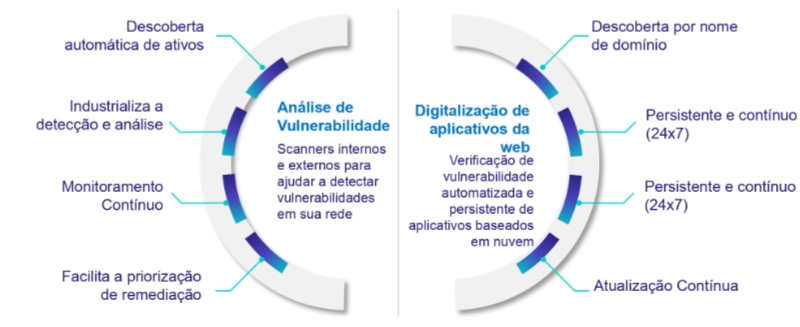
Our Differentiators
VULNERABILITY MANAGEMENT LIFECYCLE
Integrated with our vulnerability management lifecycle. Track your vulnerabilities from a single point of view
CENTER OF EXCELLENCE
Highly skilled operations team at our Global Center of Excellence
VA SCANNER SOLUTIONS
Integration of high-tech VA scanner solutions.
X-VRM: Penetration Testing and Red Team Assessment
Gain the knowledge, experience, and efficiency to conduct comprehensive adversarial security testing with actionable results.
Penetration Test
Reveal vulnerabilities that an attacker could exploit to gain access to your environment and systems.
Get equipped with personalized, actionable recommendations and guidance for remediation.
Red Team Assessment
Test your defensive and response capabilities against a simulated real-life opponent.
Understand your ability to resist social, physical, network, and application attacks.
Our Differentiators
VULNERABILITY MANAGEMENT LIFECYCLE
Integrated with our vulnerability management lifecycle. Track your vulnerabilities from a single point.
RESULTS AND EXECUTIVE SUMMARY
Final reports containing detailed findings and executive summary
SECURITY EXPERTS
Delivered by a highly qualified team of security experts
Our Differentiators
AST
Guidance and recommendations from our AST experts to improve your security posture
WEB SERVICES AND API FRAMEWORKS
Many support web services and API frameworks
SECURITY EXPERTS
End-to-end assurance as a best practice in AST using multiple technologies at different points in the SDLC
X-VRM: Application Security Testing
Protect your web applications, mobile applications and APIs by improving your security posture by identifying vulnerabilities during the systems development cycle
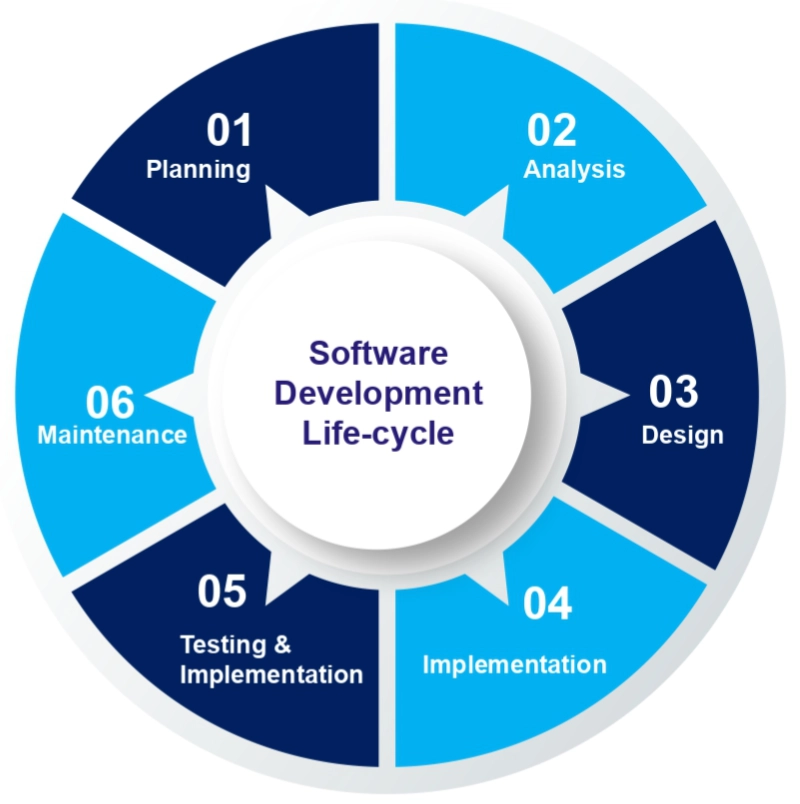
Development
Static Code Analysis
SAST, SCA
Real-time security feedback as the application is being implemented.
Pre-production
Dynamic and interactive code analysis
DAST, MAST, IAST
Testing the functional requirements of your applications, finding and fixing vulnerabilities in early stages of development before they become security risks.
Production
Runtime Application
Self-Protection
SAST, SCA
Detect and block attacks on your applications in real time without human intervention
Our Differentiators
The service leverages our CTI to explore new engagement
Center of Excellence to Leverage Broad Threat Visibility
Weekly scan for latest unconfirmed IoAs, TTPs and IoCs
Integrated with X-Secure portfolio to connect with DFIR and threat monitoring
X-VRM: Managed Threat Hunting
Expand your detection capabilities with proactive threat hunting to explore ongoing signs of compromise in your network
Leverage our CTI malware and hacking experts to detect ongoing breaches unnoticed by your security controls.
Explore the latest TTPs, helping you reduce breach dwell time, minimize impact, and provide feedback to your detection engineering
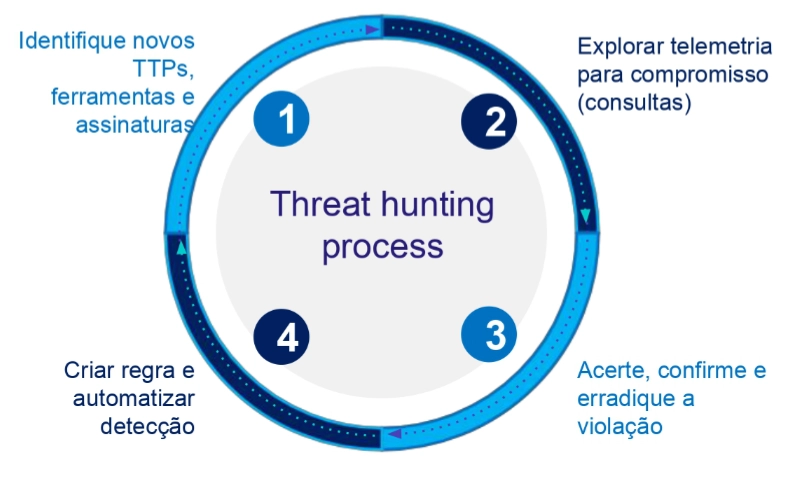
X-VRM
- Identifying and managing vulnerabilities to prevent cyber attacks.
- Penetration Tests & Offensive Security
- Managed Threat Hunting

